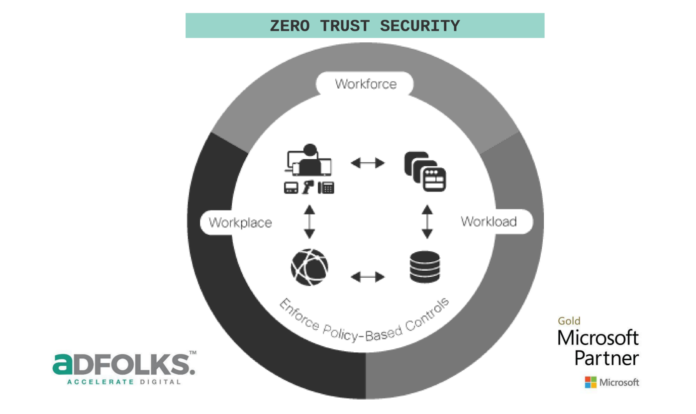
Cybersecurity is well-understood by today’s Internet and computer users. Many businesses understand the need to safeguard their networks and websites from hackers and other dangerous components and update their computer systems regularly to prevent infection. We all know what cybersecurity is, but many people have no idea how complicated it is. To understand more about the cybersecurity framework and why it’s essential to learn about it, continue reading.
Numerous individuals have varying perspectives on cybersecurity and what you should study about cybersecurity and its innumerable facets. Many individuals have a misunderstanding of what cybersecurity is. There are many things that individuals may take to increase their knowledge of various areas of a cybersecurity framework.
- What does cybersecurity entail?
Information technology (IT) security is the process of protecting computer equipment, software, and data against cybercrime. It protects data centers and other electronic systems from unauthorized access by both individuals and businesses. Effective cybersecurity can protect against malicious attacks on a company’s or a user’s networks and sensitive information, among other things. Security also protects against attacks that aim to disable or degrade the performance of a system or device.
- How critical is cybersecurity?
With more people, devices, and programs in modern businesses and an influx of data — much of it sensitive or private – cybersecurity is becoming more critical. Complicating matters is the growing sophistication of cyber attackers and their attack techniques.
- How does cybersecurity work, and what components are involved?
Secrecy programs need collaboration across many divisions of an organization. Among them are the following:
- Securing applications
- Security of information or data
- Network protection
- Planning for disaster recovery/business continuance
- Security in the workplace
- Cloud computing security
- Securing key services
- Physical protection
- Education of the end-users
Cybersecurity is a concern for all companies operating in an ever-changing security landscape. It is no longer acceptable to protect systems against known threats while leaving more esoteric threats undefended. To keep pace with changing security risks, a more proactive and flexible approach is needed. Numerous top cybersecurity consulting companies are available to help. According to the National Institute of Standards and Technology, defensive measures against known and unexpected risks include continuous monitoring and real-time assessments (NIST).
- What are the benefits of cybersecurity?
Enhancing cybersecurity processes offers several benefits.
- Enterprise-level cybersecurity.
- Protection of the system and data.
- User contact that is not allowed is blocked.
- Reduced time required for breach healing
- Security of endpoints and users.
- Adherence to regulations.
- Business continuity
- Constructing relationships of trust with developers, collaborators, customers, sponsors, and employees.
- What kind of cyber threats exists?
It’s challenging to stay current on emerging technologies, security trends, and threat information. It is necessary to protect data and other assets against cyberattacks.
Cyberthreats include the following:
- Malware is a kind of malicious software that may cause harm to a computer user. Worms, viruses, Trojan horses, and spyware are all types of malware.
- Social engineering is a kind of attack that uses human interaction to convince users to break security rules to get sensitive information.
- Phishing is a kind of social engineering in which fraudulent emails or messages are sent, seemingly from genuine sources. Their objective is to steal sensitive information such as credit card numbers or usernames and passwords.
- DDoS attacks occur when many systems disrupt the traffic of a single target system, such as a server, website, or other network resources. By flooding the target system with messages, connection requests, or packets, attackers may cause the system to slow down or crash.
- APTs are long-lasting targeted attacks in which an attacker infiltrates a network and takes data.
- A man-in-the-middle (MitM) attack occurs when an attacker intercepts and transmits communications between two parties who believe they are talking.
- Botnets, drive-by-downloads, exploit kits, malvertising, vishing, credential stuffing, XSS, SQL injection, BEC, and zero-day vulnerabilities are often used in assaults.
Numerous books are available to help you learn more about the cybersecurity framework. It’s always beneficial to be informed so that you’re aware of when to act. It is essential to understand which threats are real and which are not. If you do not educate yourself, you and your computer may be at risk. You should consult the websites of the Federal Bureau, the Cybersecurity Enhancement Program (CSP), the Department of Homeland Security, and the Federal Trade Commission. These are critical because they keep you informed on the state of cybersecurity in the United States. Additionally, they’re great resources for learning about the many cybersecurity companies available. Continue reading to discover more about a few of these companies.
Bottom-line
Many people are ignorant of the vulnerability of their PC. Even if a person thinks they are immune, many people acquire a virus or other illness daily. To ensure the security of your computer, you must educate yourself about the cybersecurity framework. There are many resources accessible to you; make use of them whenever necessary. Don’t miss this opportunity to learn about cybersecurity and how to prevent it.